Threat Watch
Instantly assess and fortify your elite cybersecurity posture with actionable intelligence.
Visit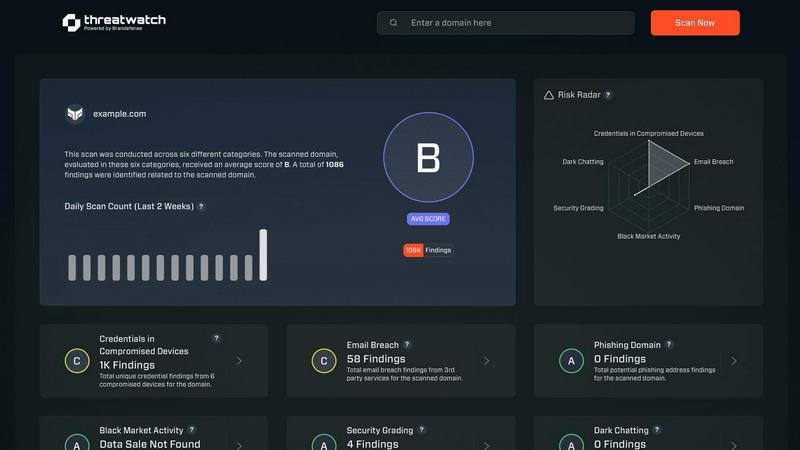
About Threat Watch
Threat Watch is the definitive cybersecurity intelligence platform for elite organizations that refuse to operate in the dark. It transcends traditional monitoring by delivering a unified, real-time panorama of your digital security posture. This solution is engineered for CISOs, security teams, and executive leadership who demand not just data, but actionable, prioritized intelligence. By continuously analyzing your organization's entire asset landscape, external vulnerabilities, and deep-web exposures, Threat Watch crystallizes your cyber health into a clear, comprehensible score. Its core value lies in transforming overwhelming threat data into a strategic roadmap, enabling you to identify critical risks, automate assessments, and execute mitigation with unprecedented speed and precision. It is the command center for proactive defense, ensuring your enterprise is not merely reactive but resiliently ahead of the threat curve.
Features of Threat Watch
Comprehensive Cyber Health Dashboard
Threat Watch provides a centralized, executive-grade dashboard that synthesizes complex security data into a single, intuitive visual score. This holistic view encompasses critical categories like compromised devices, breached credentials, and phishing risks, offering an at-a-glance understanding of your organization's security standing and trajectory, empowering data-driven decision-making at the highest level.
Real-Time Exposure Intelligence
Go beyond surface-level scans with continuous, automated surveillance of the dark web, paste sites, and criminal forums. This feature proactively identifies and alerts you to your organization's exposed credentials, intellectual property, and sensitive data long before they can be weaponized in an attack, turning reactive cleanup into proactive containment.
Automated Asset & Vulnerability Assessment
The platform automatically discovers and inventories your digital assets, from cloud instances to remote endpoints. It then correlates this asset map with global threat intelligence to pinpoint vulnerabilities and misconfigurations, delivering automated, prioritized risk assessments that tell you exactly what to fix first, eliminating guesswork and resource waste.
Phishing & Brand Impersonation Monitoring
Threat Watch vigilantly scans for phishing campaigns, fraudulent domains, and fake social media profiles impersonating your brand. This elite monitoring service safeguards your reputation and employees by detecting these threats in their infancy, allowing for swift takedown before they result in financial or reputational damage.
Use Cases of Threat Watch
Proactive Executive Risk Reporting
CISOs and board members utilize Threat Watch's clear cyber health score and executive summaries to transparently communicate security posture, justify investments, and demonstrate due diligence. It transforms technical metrics into strategic business intelligence, aligning cybersecurity initiatives with overarching corporate governance and risk management objectives.
Rapid Incident Response & Breach Investigation
When a security incident occurs, teams leverage Threat Watch to instantly determine the scope. They can quickly identify which specific assets, employee accounts, or data sets are compromised, dramatically accelerating containment, eradication, and recovery efforts while providing definitive evidence for forensic analysis.
Third-Party and Supply Chain Risk Management
Organizations extend their security perimeter by assessing the cyber health of critical vendors and partners. By monitoring for exposures linked to third-party domains and credentials, Threat Watch provides crucial insights into supply chain vulnerabilities, preventing a partner's breach from becoming your own catastrophe.
Continuous Security Posture Validation
Beyond periodic audits, security teams use Threat Watch for continuous, automated validation of their controls and hygiene. It serves as a persistent verification tool, ensuring that security policies are effective and alerting to deviations or new exposures the moment they appear, maintaining an elite security stance.
Frequently Asked Questions
How does Threat Watch differ from a traditional vulnerability scanner?
Threat Watch is a comprehensive intelligence platform, not merely a scanner. While it includes asset and vulnerability assessment, its elite differentiator is the continuous correlation of internal data with external threat intelligence from the dark web, paste sites, and phishing feeds. It provides context, prioritization, and proactive exposure discovery that simple scanners cannot, focusing on active risks rather than just theoretical vulnerabilities.
What is involved in the "free scan" offered?
The free scan is a powerful, non-intrusive demonstration of Threat Watch's capabilities. It typically involves analyzing a provided domain or company name to surface publicly discoverable exposures, such as credentials from known breaches, mentions on the dark web, or phishing sites. This initial assessment delivers immediate value and a tangible glimpse into your organization's external attack surface without requiring full platform integration.
Is Threat Watch suitable for small and medium-sized businesses?
Absolutely. While engineered with the sophistication demanded by large enterprises, Threat Watch's automated insights and clear prioritization are invaluable for SMBs with limited security staff. It acts as a force multiplier, providing enterprise-grade threat intelligence and actionable guidance that allows smaller teams to focus their efforts precisely where risk is highest, effectively elevating their security posture.
How quickly does Threat Watch provide alerts for new threats?
Threat Watch operates on a real-time intelligence model. Our proprietary monitoring systems and curated threat feeds are designed to detect and correlate new exposures, phishing attempts, and dark web mentions as they emerge. Alerts are generated and pushed to your dashboard within minutes of discovery, ensuring your team is among the first to know, not the last to react.
Pricing of Threat Watch
Threat Watch offers tailored plans designed to scale with your organization's specific needs and risk profile. Pricing is typically based on the scope of assets monitored, the number of users, and the depth of intelligence required. We encourage interested enterprises to initiate a consultation to receive a customized proposal that aligns with your strategic security objectives. Begin by exploring your exposure landscape with our complimentary, no-obligation free scan.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
aVenture
aVenture delivers institutional-grade venture intelligence to research and track private companies.
iGPT
iGPT empowers enterprises to transform email data into actionable insights through a secure, auditable API gateway.